The doorbell rings. You open the door and see a gentleman who, in a fun way, wants to help you learn Chinese. Your dream has come true!
However, after a while at home, you realize that the unexpected guest has vanished along with your laptop and several other valuable items. You then find them on the virtual marketplace.
That can happen after installing unverified third-party apps on devices in the Google domain. Excessive permissions granted to them can threaten the cybersecurity of the entire school.
From this post, you’ll learn:
- What’s the difference between first-party and third-party applications
- What risks to your domain cause the lack of control over third-party apps
- How to manage and audit third-party apps in your Google domain step-by-step
First-Party vs. Third-Party Applications
Let’s start by distinguishing between first and third-party applications. Knowing this difference helps us anticipate the potential challenges these apps pose before organizations use each.
▫️ First-Party Apps: You or your organization created and owns them. They are usually designed to meet the owner’s specific needs and are used only on your devices. They don’t pose significant security risks as you fully control their development and permissions.
▫️ Third-Party Apps: Someone other than the manufacturer of your device or the creator of the operating system (developers, vendors, companies) made and owns them. These apps offer additional features and are available for installation from external sources such as the Google Play Store.
Risks of Uncontrolled Third-Party Apps for Your Domain
You might have heard about the White House policy banning TikTok on government devices. In 2023, the Biden administration identified this Chinese video app as a threat to US user data. This assumption was based on the possibility of sharing user information collected by ByteDance, the owner, with the Chinese government for disinformation or intelligence purposes.
Indeed, unverified third-party applications can put your user data and online resources at risk. When installing new applications, users usually grant them specific access. Excessive permissions may significantly affect the device’s cybersecurity and make the entire Google domain vulnerable.
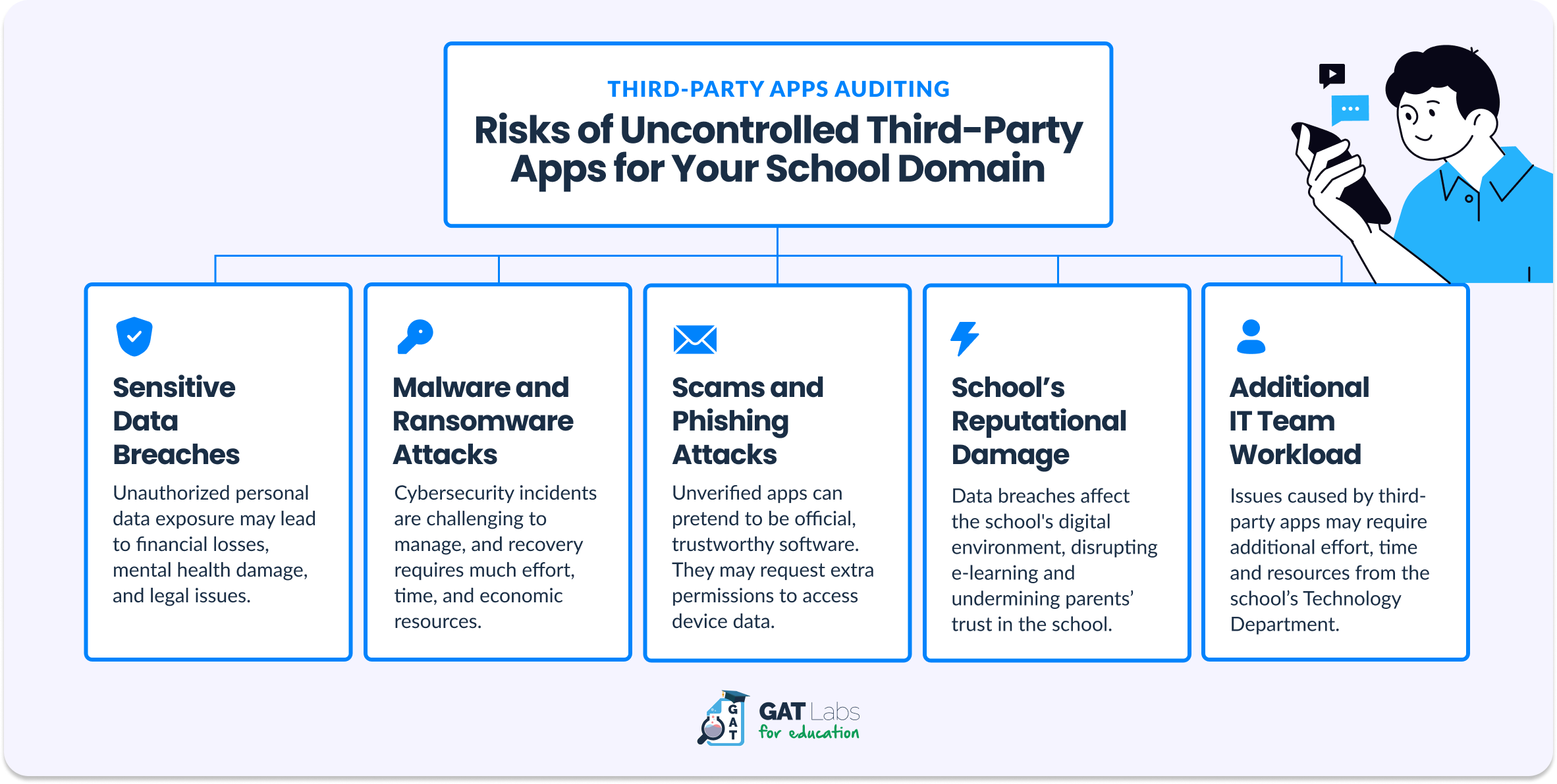
▫️ Data Breaches. Unsecured apps can leak your school’s sensitive data, such as addresses, Social Security numbers, or credit card numbers. Unauthorized personal data exposure may lead to financial losses, mental health damage, and legal issues.
▫️ Malware and Ransomware Attacks. Cybersecurity incidents vary in scope and impact across the school domain and always incur additional costs. These attacks are challenging to manage, and recovery requires much effort, time, and economic resources.
▫️ Scams and Phishing Attacks. Unverified apps can pretend to be official, trustworthy software. They may request additional permissions to access device data or control the screen, enabling them to steal login credentials and other personal information from users.
▫️ Reputational Damage. Data breaches and other cybersecurity incidents affect the school’s digital environment, disrupting e-learning. Parents and the local community may lose trust in the school, which is responsible for ensuring student safety and security.
▫️ Additional IT Team Workload. Issues caused by third-party apps may require additional effort from the IT team. Dealing with an incident and reinforcing security measures consumes many resources, which can weaken other aspects of the school’s cybersecurity posture.
Manage your Third-Party Apps Step-by-Step
Now, let’s get to the gist of this article.
School admins may wonder: How do I manage third-party apps for all users in Google Workspace for Education? How can I restrict them to strengthen school cybersecurity while respecting data privacy?
It sounds challenging, but an effective plan and robust auditing tools streamline this task. Follow these three steps to optimally manage third-party apps in your Google domain.
1. Audit Third-Party Apps
The first step to improving your school’s third-party app policy is to assess where you are today. Auditing the current state of installed applications on user accounts will allow you to evaluate risk and schedule appropriate actions.
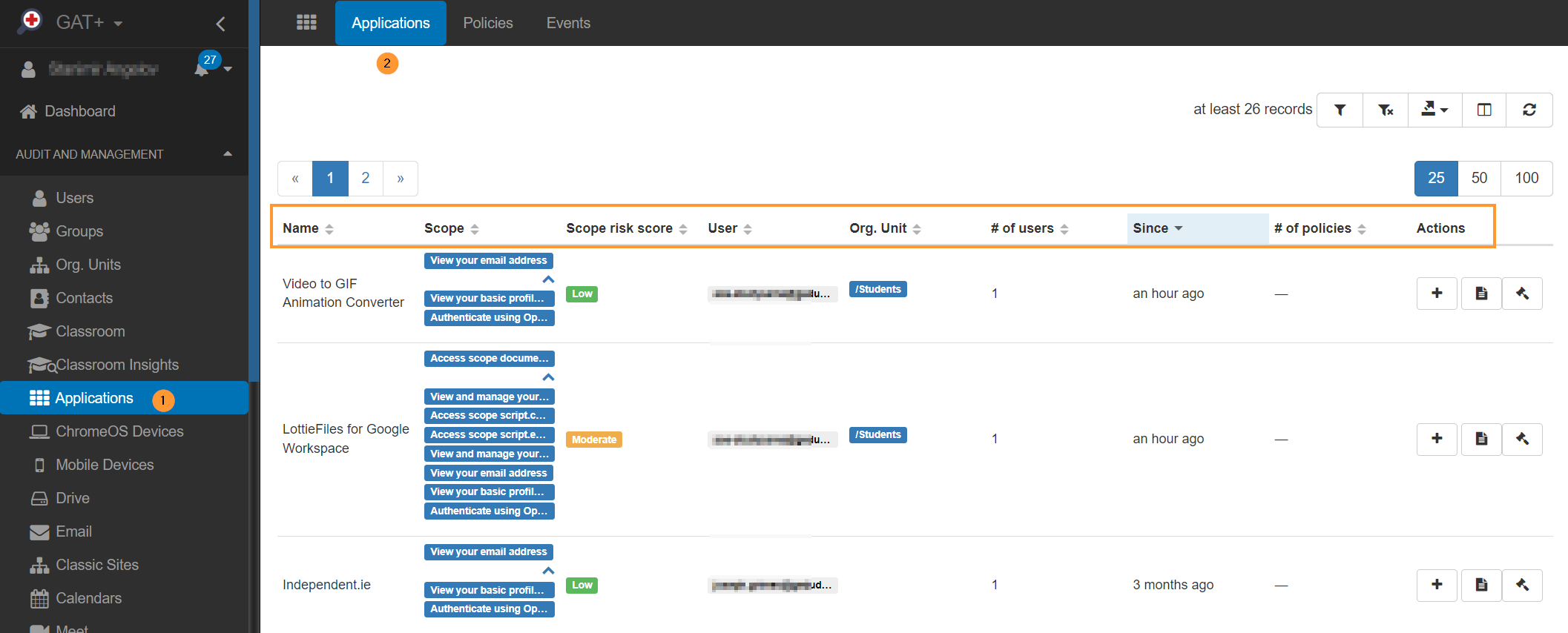
Application risk assessment provided by GAT+ enables admins to review all applications installed in your Google domain, how many users installed them, and – most importantly for security – what privileges each app has requested.
While some privileges pose little to no risk to your data security, others can significantly impact your domain. The GAT+ report shows the scope risk score for each application based on the privileges granted. Moderate and high scores should alarm you and make you consider whether these applications should be removed.
2. Restrict Google Services Access
Before taking any action to manage existing applications, you can strengthen the security of your Google Workspace services globally. To achieve this, enter the Admin console and restrict access to selected Google services to only apps configured with a Trusted access setting.
This action disables apps with a Limited access setting from accessing specific Google service data. They can now access only unrestricted services. You can modify their permissions anytime.
Google Admin console allows you to control third-party access to Google services data and tailor a message when a user tries to install an unauthorized app. For more advanced and code-free functionalities to manage third-party apps, look at the next step.
3. Set up Third-Party Apps Access Policies
Let’s go back to the Application section in GAT+, where we can see all apps installed by domain users and their permissions. Once Admins have reviewed the scope risk score of each app, they can decide which policy to apply to it.
-
Banned Third-Party Apps Policy
School admins may consider banning apps with medium- and/or high-risk scores to decrease cybersecurity threats. For this purpose, GAT+ offers a real-time third-party app banning feature.
It’s a proactive action based on the user behavior. After setting up ban policies for specific applications and users, the apps can’t be used anymore, and their permissions are revoked. Whenever a user wants to install an app or grant access again, the admin gets a notification, and GAT disables the user’s action.
-
Trusted Third-Party App Policy
Admins may want to enable some apps for specific users. They must apply the Trust policy to a given app and users or groups. It will remove selected users from the Ban policy. This way, a single app can be partially banned and partially trusted.
For example, the YouTube app can be banned for the entire school, but some teachers can access it from their devices thanks to the Trust policy.
Check how to add and remove third-party app policies and what no data on a specific app in the application audit means in our Knowledge Base.
Closing Thoughts
The effects of uncontrolled third-party applications installed by your users can be painful. Reduce cybersecurity risks and avoid extra burdens by implementing real-time audits and policies to protect sensitive data in your Google domain.
–––
Looking for more practical hints and tips to improve your domain management? Elevate your Google Workspace for Education auditing today by following the steps in our guide for school admins.
Join our newsletter for practical tips on managing, securing, and getting the most out of Google Workspace, designed with Admins and IT teams in mind.