Gone are the days of siloed data and desktop-bound documents. Today’s organizations are increasingly migrating their workflows to cloud-based platforms like Google Workspace. While the convenience and collaboration benefits are undeniable, it’s crucial to remember that security in the cloud is just as important as security on-premise.
That’s why access management is one of the most critical aspects of cloud security. This type of audit ensures that only authorized users have access to specific data and resources within your Google Workspace environment.
But how do you know if your access controls are working effectively? This is where access management audits come in.
Note: This is the first blog in our series about making your Google Workspace safer. Keep an eye out for more helpful tips coming soon!
What is an Access Management Audit?
Access Management Audits are key to keeping your Google Workspace secure. They ensure that only the appropriate individuals have access to the information they need for their roles. Furthermore, these audits are crucial for maintaining the safety of your workspace.
But, what does the access management audit process include?
- – Identifying all users and their roles: This step is crucial for understanding who can access what within your Workspace, clearly delineating permissions across different levels (administrator, editor, viewer).
- – Evaluating access permissions: Assess whether the access granted aligns with the individual’s role within your organization, aiming to minimize risks of unauthorized access.
- – Reviewing access logs and activities: This process helps in spotting any unusual or suspicious user activities that might suggest potential security breaches.
The Unmatched Benefits
Implementing regular access management audits within your Google Workspace can significantly bolster your security posture. Here are the key advantages:
- – Enhanced Security: Tighten your defense against data breaches, accidental leaks, and malicious insider threats.
- – Improved Compliance: Stay aligned with regulatory requirements, such as GDPR and HIPAA, through robust access controls.
- – Mitigation of Insider Threats: Detect and address potential insider threats through analysis of access patterns and behaviors.
The Risks of Overlooking Access Management Audits
Failing to conduct regular audits leaves your organization vulnerable to a broad spectrum of risks, including cyberattacks, regulatory fines, data breaches, and interruptions in operations. Such vulnerabilities can significantly damage your organization’s reputation and financial health, particularly in industries subject to rigorous regulatory oversight.
But fear not, we are here to help.
Best Practices for Effective Audits
Implementing a set of best practices is essential for every Google admin. These practices are the building blocks for constructing a secure, compliant, and efficient audit system within your Google Workspace.
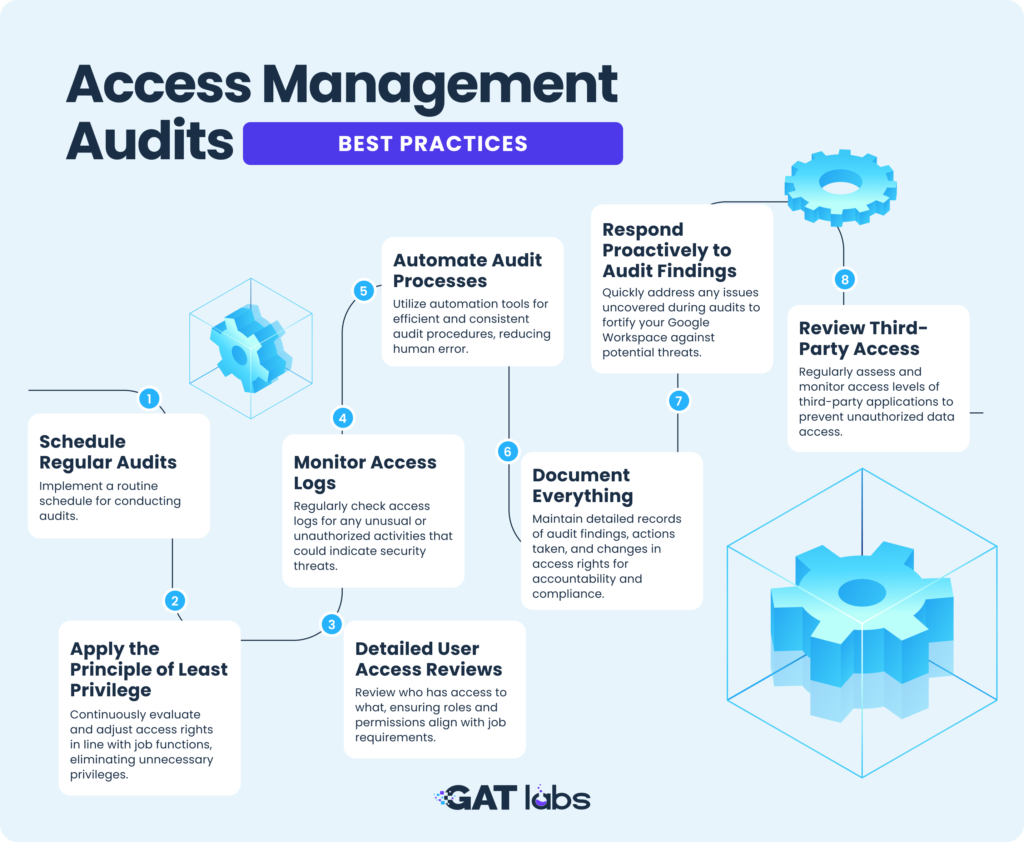
Our infographic above provides a clear visual summary of the essential actions required for a thorough and effective access management audit. By following these guidelines, you can establish a robust framework for monitoring and managing user access in your digital workspace.
Highlighted Best Practices:
- – Regular Review Cycles: Keeping your audits on a consistent schedule guarantees that your security measures evolve with your organization’s needs and external threats.
- – Principle of Least Privilege: Regularly assessing user permissions. This ensures that access is granted strictly based on necessity, thereby reducing exposure to potential security breaches.
- – Comprehensive Reporting: A meticulous approach to documenting audit processes and outcomes is crucial for transparency, accountability, and regulatory compliance.
Empowering your Auditing Strategy
Recognizing the complexities of access management audits in Google Workspace, GAT Labs offers a meticulously crafted Google Workspace Auditing Guide tailored for administrators like you. This essential 10-step guide demystifies the process, empowering you to conduct comprehensive and effective access management audits with ease.
The guide equips you with:
- – Detailed Checklist: Navigate through the audit process with confidence, covering all vital aspects to ensure no stone is left unturned.
- – Best Practices and Recommendations: Equip yourself with the knowledge to implement robust access controls. By doing so, you fortify your Google Workspace against unauthorized access and potential security threats.
- – Actionable Insights: Master the art of interpreting audit findings. For Google admins, this is extremely beneficial to enable you to take decisive, corrective actions to bolster your security posture.
With our Google Workspace Auditing Guide, auditing becomes not just manageable, but a powerful facet of your overall security strategy. Unlock these insights and transform the way you secure your digital workspace today.

Conclusion: The Imperative of Proactive Security
In the ever-evolving landscape of cloud computing, the security of your Google Workspace environment remains paramount. Indeed, access management audits are not merely a procedural necessity; they are a critical defense mechanism against the increasing sophistication of cyber threats. By embracing a proactive approach to security, underscored by the regular conduct of these audits, you can ensure that your organization remains resilient in the face of potential vulnerabilities.
Moreover, the integration of tools and resources, such as those offered by GAT Labs, can significantly streamline the audit process. These solutions enhance the efficiency of conducting audits and provide deeper insights into your Google Workspace environment, enabling a deeper understanding of your security posture.
Taking Action
As we navigate the complexities of digital security, the role of access management audits in safeguarding our cloud environments has never been more critical.
We invite you to download your free copy of the 10 Essential Steps to Audit your Google Workspace Domain today and take control of your cloud security!
Secure your Google Workspace environment, maintain compliance with industry standards, and minimize the risk of data breaches and insider threats.
Insights That Matter. In Your Inbox.
Join our newsletter for practical tips on managing, securing, and getting the most out of Google Workspace, designed with Admins and IT teams in mind.







