We provide a new feature to report all devices used in your domain. This cloud identity audit shows a detailed view of all devices used to log in to the domain.
You can do it now with GAT+ which is a Google Workspace audit tool that provides a highly detailed internal view of the entire domain.
Devices Report #
Step 1. #
Navigate to GAT+ > Audit and management > Devices (1)
Step 2. #
Find the list of all the devices reported with Cloud Identity – devices from Google (2)
Note: This might have similar data reported in Chrome OS and Mobile device audits.

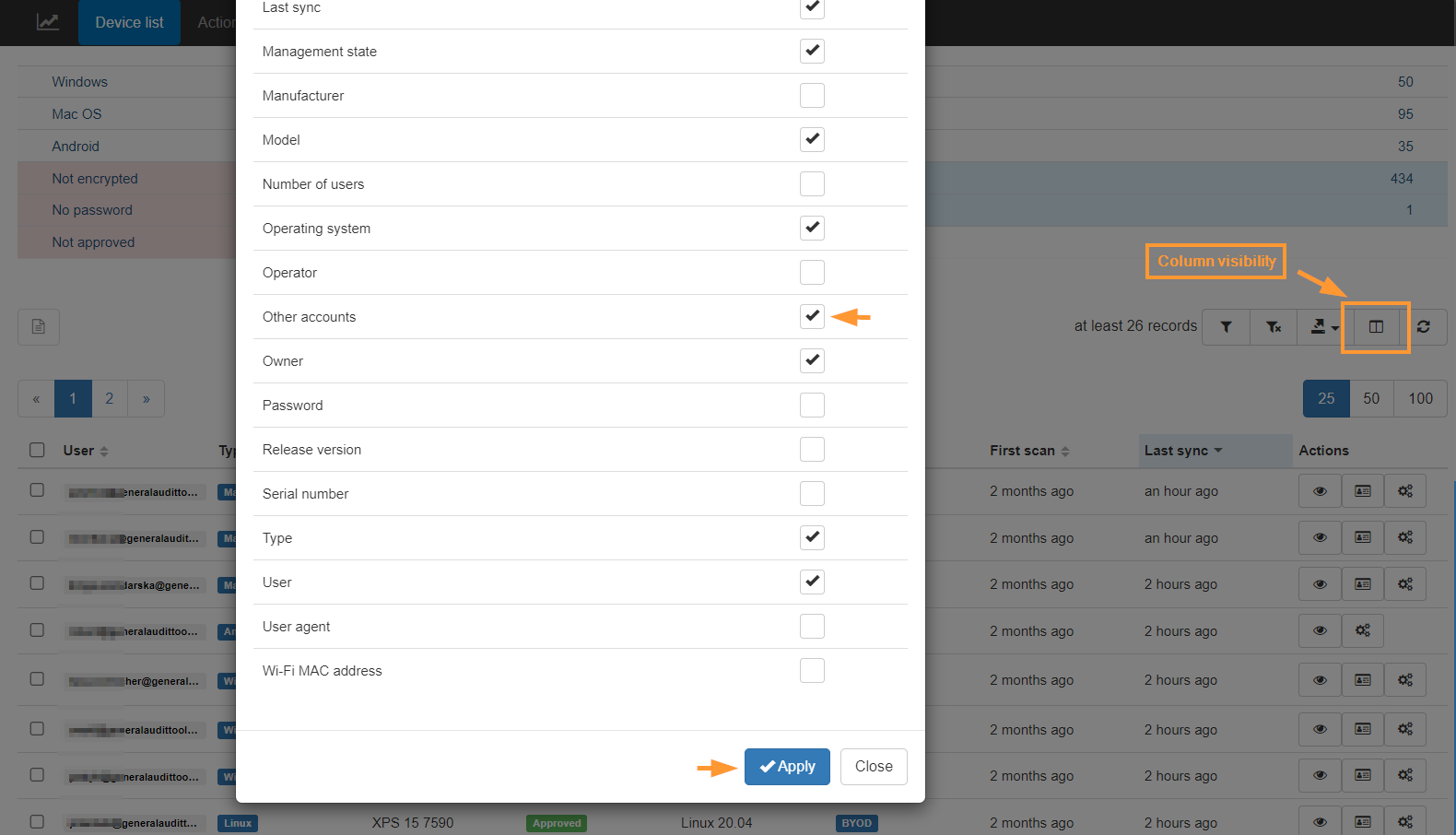
Additional columns of data #
By default only a few sections are displayed about the Devices themselves, however under the Columns visibility, more details can be displayed for auditing purposes:
- Hostname
- Last security patch
- Other accounts, and more.
Step 3. Table View #
The top table (3) will show aggregated filters.
- Type – shows devices by their type:
- Windows
- macOS
- Android
- Linux
- ChromeOS
- iOS
- Security – shows the number of devices:
- number of not encrypted devices
- number of no passwords set on the device
- number of not approved devices
- Owner – shows the owner of the devices:
- BYOD – Bring Your Device
- Company – Company-owned Device
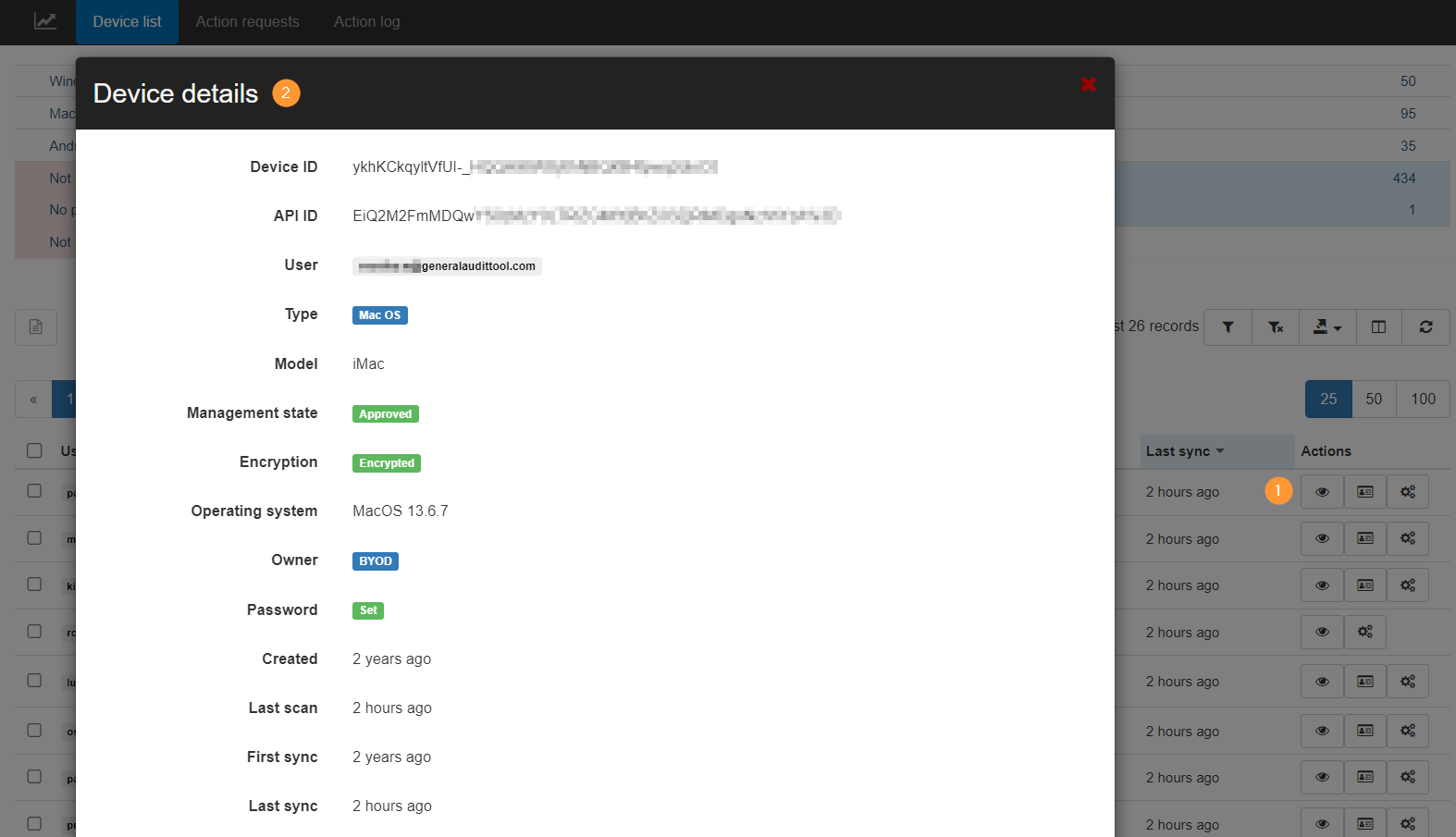
Step 4. Metadata #
Click the eye icon under Actions (1) to view all the specific device details.
The metadata will show all the users and the devices each user used to log in and access the domain.
You can view the Type of device used by each user of the domain, the Operating system, whether the device has a Password set up or not if the device is Encrypted or not, the last time the device synced to the domain, and many more filters available.
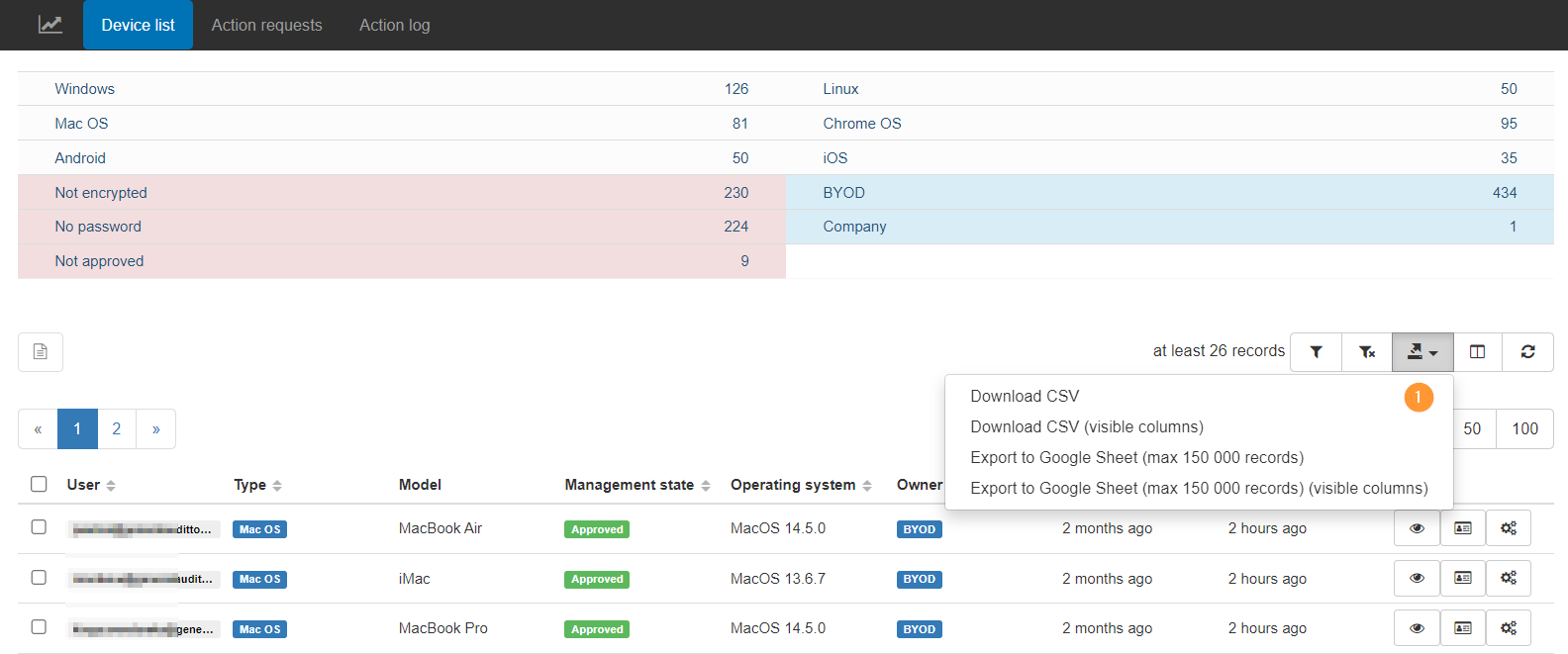
Step 5. Export data #
The data can be exported into Google spreadsheets or CSV files (1)
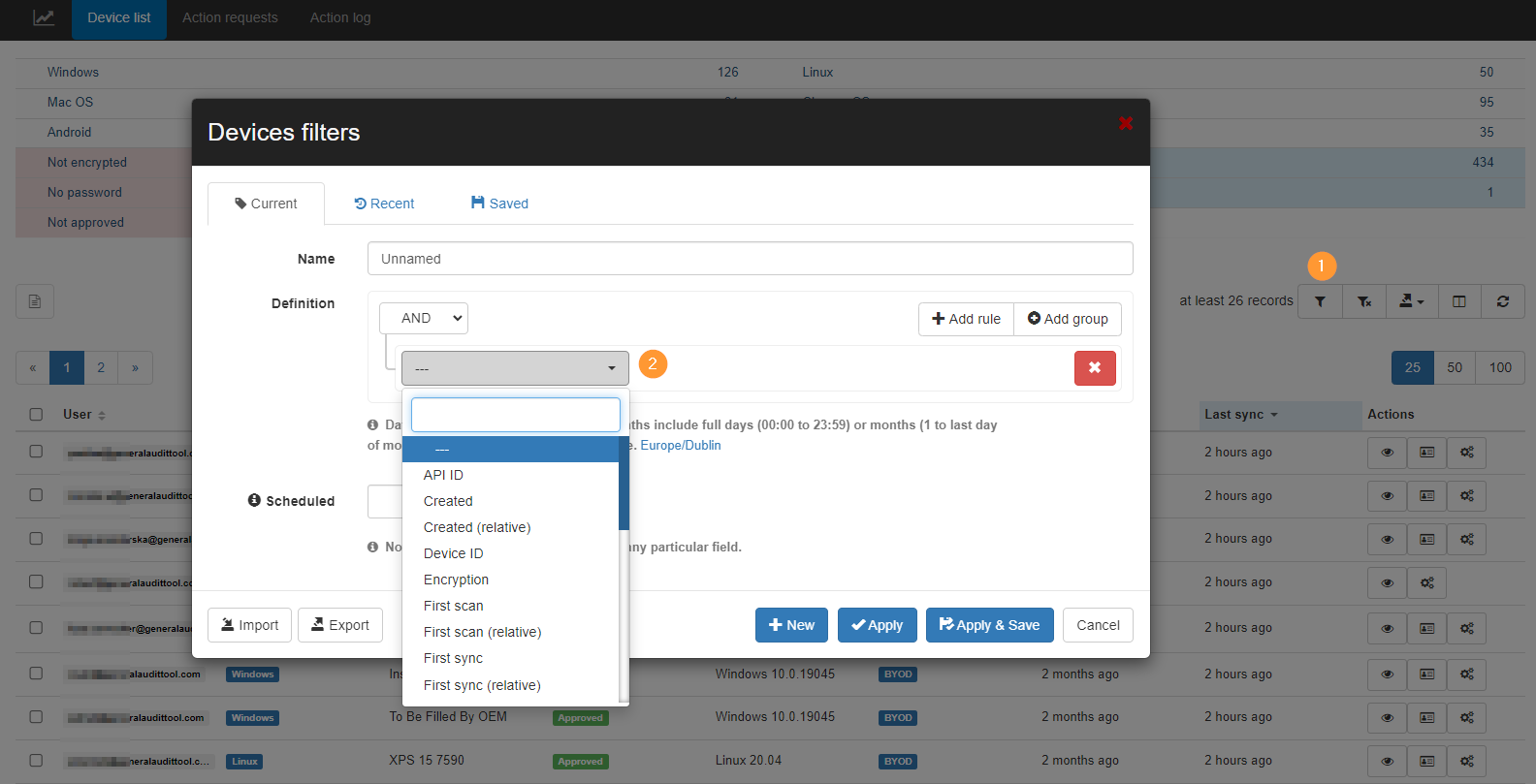
Step 6. Filters #
Multiple filters can be applied to find specific users or devices and much more.
Click on the funnel icon on the right side below (1) to define specific device filters (2)
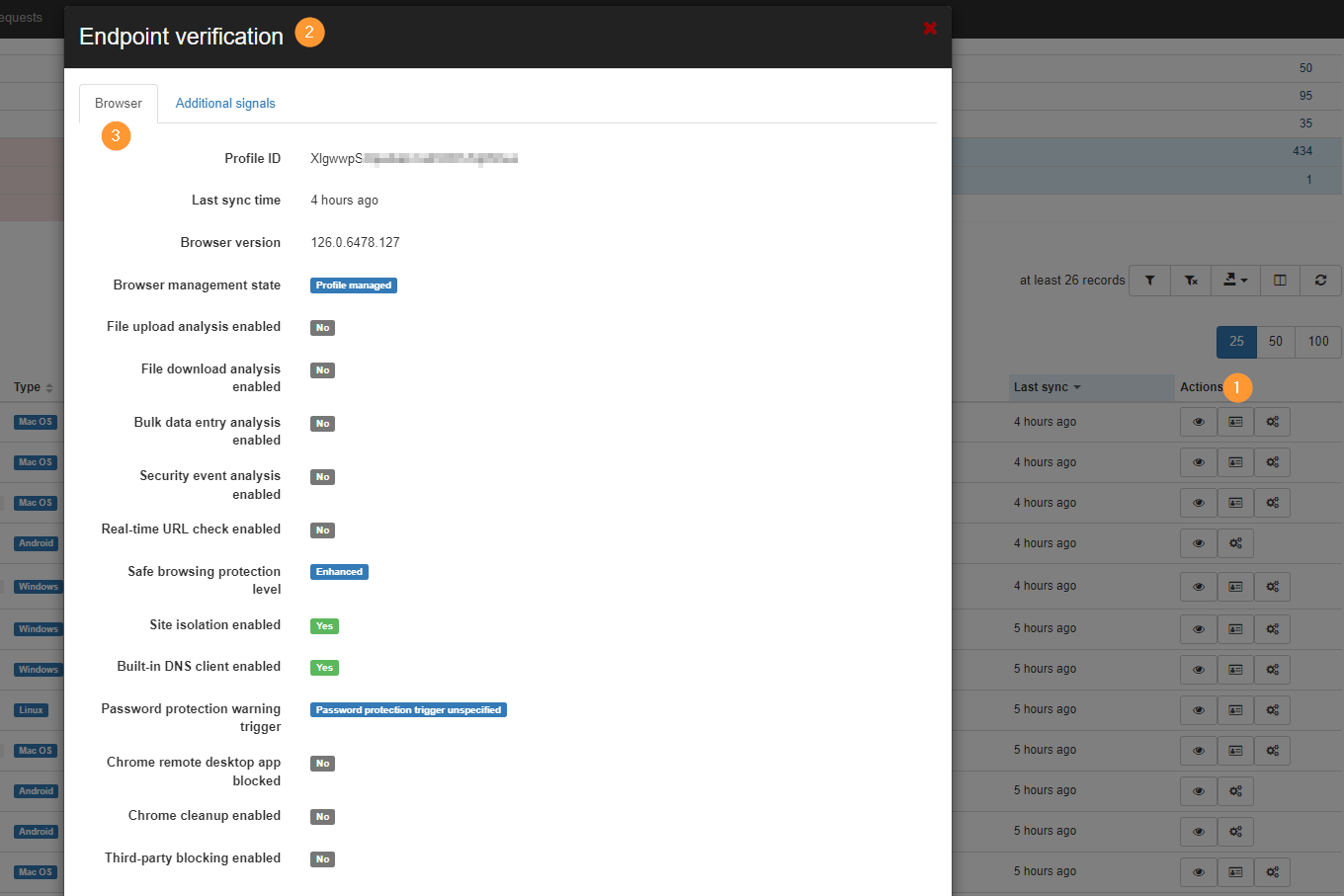
Endpoint verification details #
Audit and view all the endpoint verification details by selecting its detail view.
View the information such as Browser info reported such as Last sync time, browser version, browser management state, built-in DNS client enabled, and more.
View the Additional signals such as OS native firewall enabled, Secure boot enabled, or Windows domain name
Actions #
GAT+ empowers administrators to perform various actions on devices within the Google Workspace domain, enhancing security and control. These actions can be accessed via the Google API and are available to both Admins and Delegated Auditors.
Device Actions:
- Delete the device: Remove the device from the Google Admin Console
- Wipe the device: Erases all data on the specified device.
- Cancel the device wipe: Halts an ongoing device wipe process, applicable if the device is in a “pending wipe” state.
- The device enters the “pending wipe” state when a wipe device command is issued, but has not yet been sent to the device. The cancel wipe will fail if the wipe command has already been issued to the device.
Device User Actions:
- Approve the device user: Grants a blocked Google Workspace account access to the device.
- Block the device user: Revokes a Google Workspace account’s access to the device.
- Cancel the device user wipe: Cancels an unfinished user account wipe. This operation can be used to cancel the device wipe in the gap between the wipe operation returning success and the device being wiped
- Delete the device user: Schedules the removal of the Google Workspace account from the device.
- Wipe the device user: Erases the user’s work account data on the device, leaving personal data unaffected.
- For example, if a Gmail app is installed on a device that is used for personal and work purposes, and the user is logged in to the Gmail app with their personal account as well as their work account, wiping the “deviceUser” by their work administrator will not affect their personal account within Gmail or other apps such as Photos
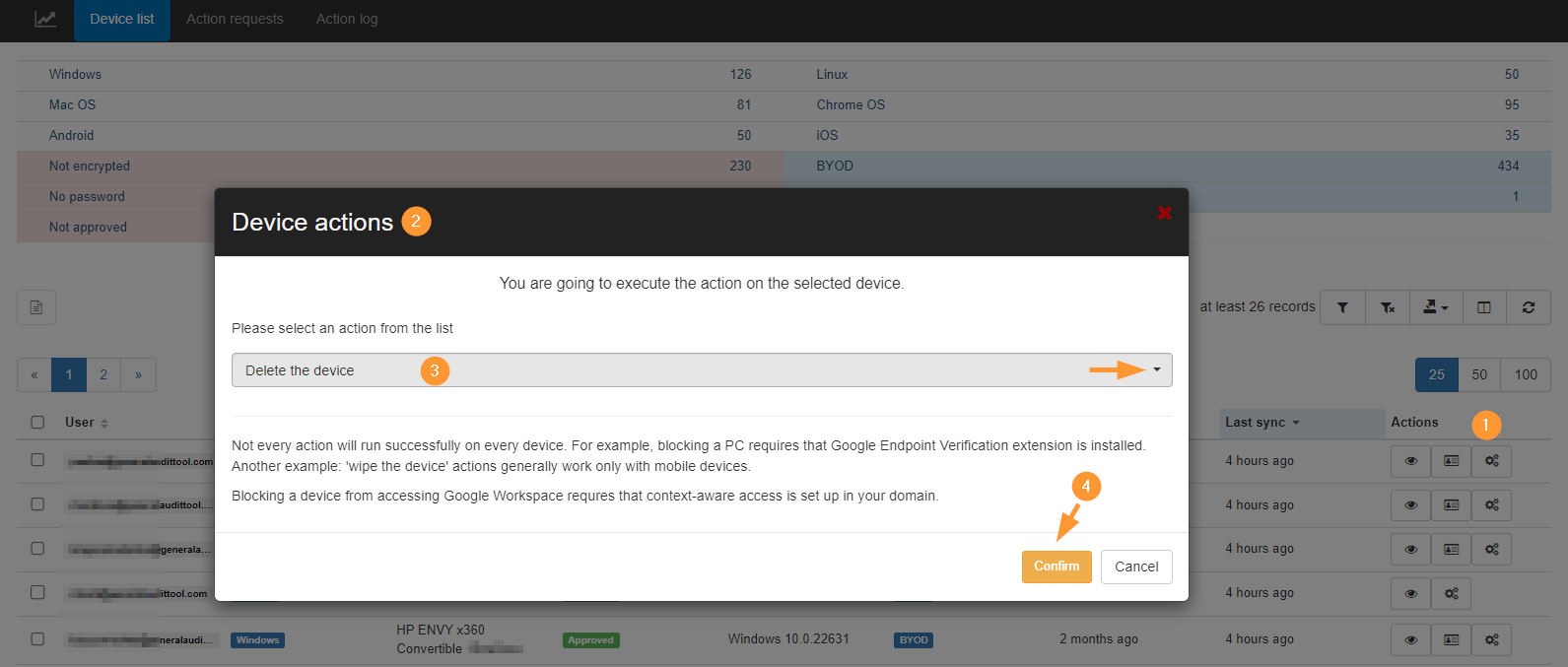
NOTE: Not every action will run successfully on every device.
- For example, blocking a PC requires that a Google Endpoint Verification extension is installed.
- Another example: ‘wipe the device’ actions generally work only with mobile devices.
- Blocking a device from accessing Google Workspace requires that context-aware access is set up in your domain.
When the action is selected click “Confirm” (4) to proceed.
Result #
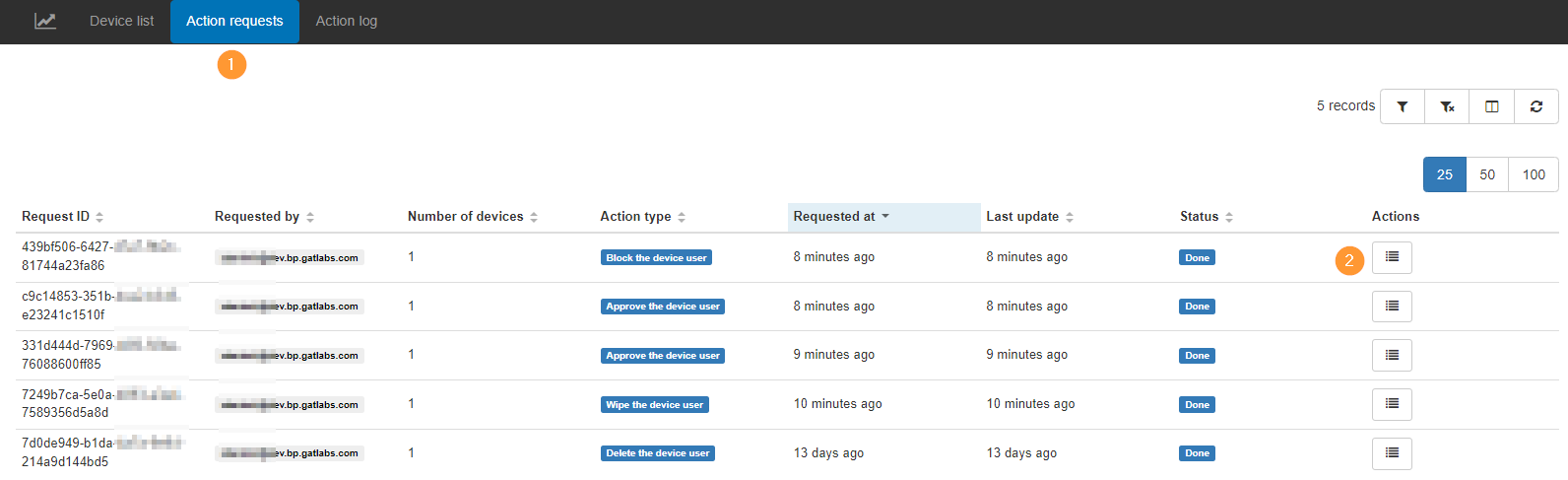
Action requests #
Action requests will show all the actions that are requested and executed.
View the number of devices, the action type, the requested at, the last update, and the Status of the job.
Under the Actions, you can see the job that is executed.
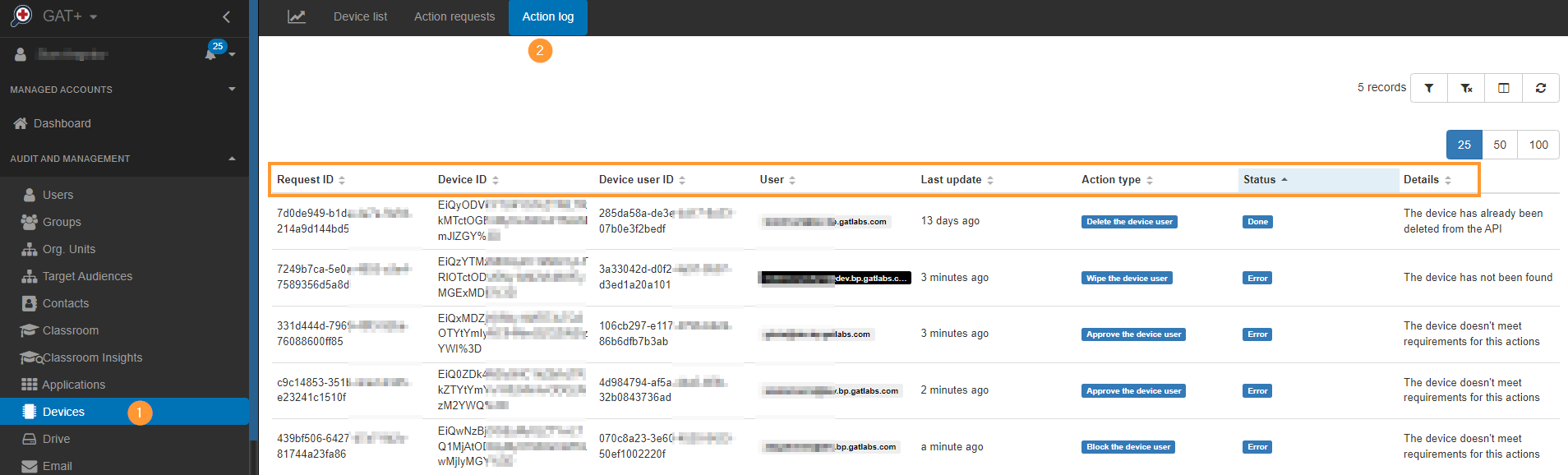
Action log #
When the action is taken the result will take into effect and will be shown in the Action log.
It could be a case where action cannot be taken and an error will be shown, the Details log will show why it failed.